Secure Your GCP: The Power of Least Privilege
Learn how to achieve the PoLP while still running your resources efficiently on GCP.
%2520(3).png)
During my journey to become a Professional Cloud Developer certified by Google Cloud, I found key insights that I will be sharing in this blog. For over three years, I have been using Firebase as my preferred Backend as a Service (BaaS) in the projects I work on. The fact that Firebase runs on Google Cloud was a decisive factor that influenced my decision to take the exam. Despite my prior experience with services like Firestore or Cloud Storage, I took a course to deepen my understanding of services I wasn't familiar with, such as Compute Engine or App Engine. One notable aspect that caught my attention during my certification study was the Principle of Least Privilege, which I’ll explain in this blog.
I’ll also go through a very important service offered by Google Cloud called Identity and Access Management and how you can use it to achieve this principle.
Principle of Least Privilege: What is it?
The Principle of Least Privilege (PoLP) underscores the importance of providing a resource, be it a Cloud Function, a Compute Engine instance, or a cluster operating on Google Kubernetes Engine, with only the minimal permissions required for its proper functioning.
You may be wondering why you should follow this principle while not giving extra permissions to your resources located on GCP. Let's delve into the reasons why this practice is significant.
For instance, think about a Cloud Function tasked with reading a file from Cloud Storage. Adhering to PoLP dictates that you provide solely the read permissions required for that specific function, avoiding unnecessary permissions such as write access. If you grant permissions to your resources that are not needed, you’re introducing potential security risks because you’ll be providing access beyond what is essential for the task at hand.
Identity and Access Management (IAM)
Identity and Access Management is a service offered by Google Cloud that gives you the ability to verify that a certain identity (it could be a user, a group of users or even an app) has the necessary permissions to access a particular resource (a virtual server, a database, etc.).
Through something called “roles”, you assign a set of permissions to an identity. GCP offers three types of roles:
Basic roles (or primitive roles): these roles are not recommended for production environments.
- Viewer: Read only access.
- Editor: Read and write access.
- Owner: Besides having read and write access, you can also manage roles and permissions and you can even change the billing configuration.
Predefined roles: Roles that are created and managed by Google for different purposes.
Custom roles: If the predefined roles offered by Google are not sufficient, you can create your own.
Now that you know the difference between the roles offered by GCP, we can continue describing how to achieve the PoLP using a simple example.
Implementation examples
Let’s consider the Cloud Function I talked about earlier in this blog. Its end goal is to read a file from a bucket located on Cloud Storage. By default, all Cloud Functions are given the same exact service account that has the Editor role. Let’s remember, that role besides including all read permissions, can modify existing resources.
Although the Cloud Function will perfectly run with that service account, it would be violating the PoLP. If we take a look at the IAM permissions related to Cloud Storage, the Cloud Function would only need the storage.objects.get permission to run as expected.
Let’s see how you can replace the permissions given by the Editor role with the one you need (we won’t cover how to deploy a Cloud Function and we will assume that it was already deployed):
- The first step would be to search for “IAM” in the Google Cloud search bar.
- Once you’re there, you’ll have to select the “Service Accounts” options located on the left side.
- Here you’ll see all the service accounts that your project has configured. To create a new service account, you have to press the “Create service account” button located at the top (beneath the search bar).
- After its initial configuration where you set the name and a description (the ID will be populated automatically but you can change it), Google Cloud will ask for the role you want to assign to that service account. Here we will use a predefined role offered by Google called “Storage Object Viewer” that has the storage.objects.get permission we need.
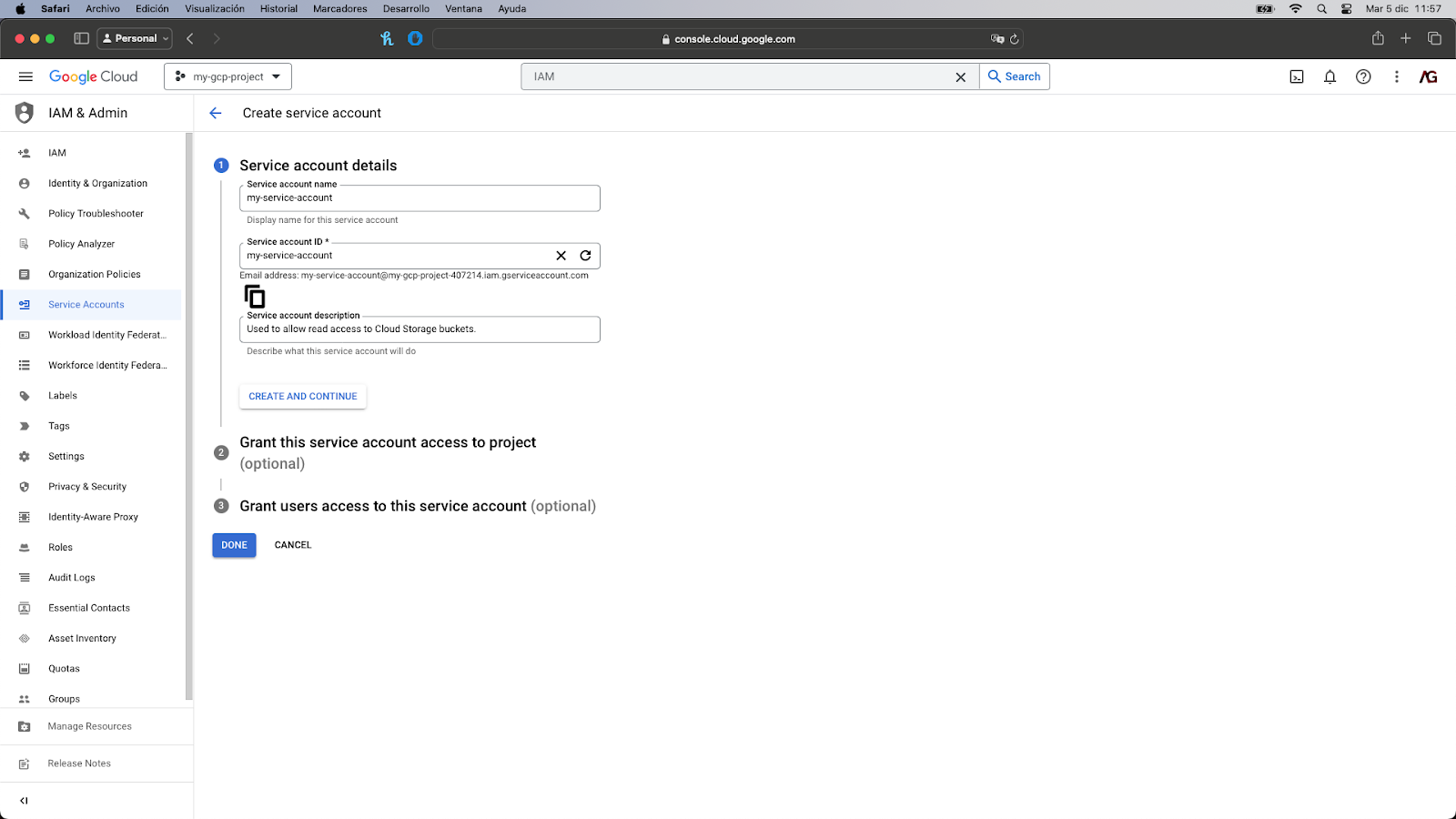
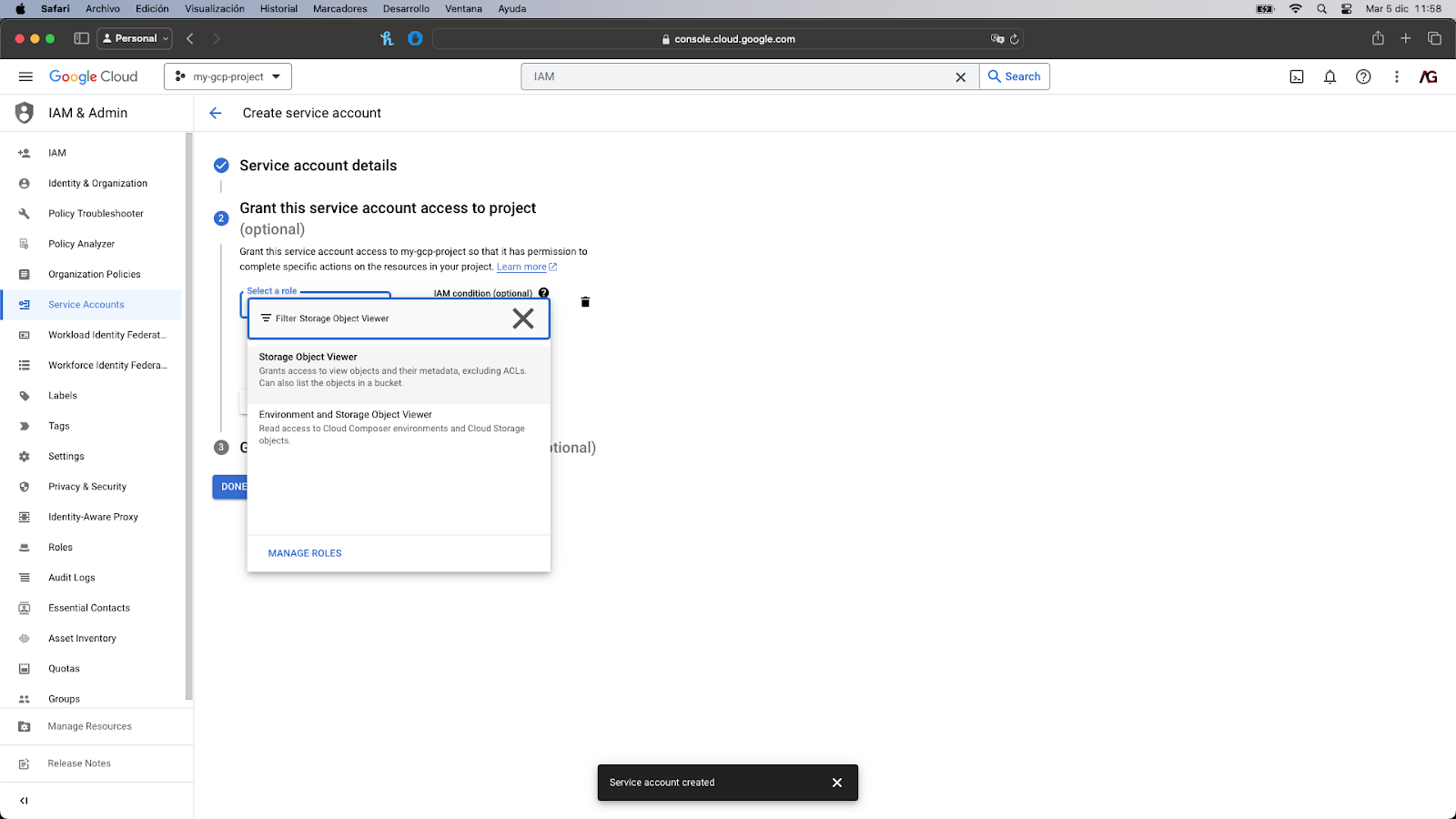
- You can avoid the last step since we don’t need it for the correct execution of our Cloud Function. All you have to do is click on the “Done” button located at the bottom.
- Once the service account is created, you’ll set it listed. An email address was associated with it for identification purposes. Now, we have to search “Cloud Functions” in the search bar.
- Search for the Cloud Function you’d like to edit.
- Click on the “Edit” button located at the top (beneath the search bar).
- Click on the “Runtime, build, connections and security settings” dropdown to open it.
- Under the “Runtime” tab, click on the Service account dropdown and search for the service account you created on the previous step.

- You’ll then have to click on Next and then Deploy. The Cloud Function would be redeployed with the updated service account.
And that’s it! The Cloud Function has associated with it the newly created service account and it follows the PoLP principle!
Now let’s suppose you need to implement a new requirement: The Cloud Function has to write some results after reading the file. The good news is that you don’t have to create a new service account. Google Cloud offers the possibility to edit service accounts and add or remove permissions as needed.
- Go to IAM.
- Under the IAM tab, search the service account you want to edit by its email address and click on the pencil icon located at the right.

- Click on the “Add another role” button and search for the Storage Object Creator role. This is also a predefined role that has the storage.objects.create permission.
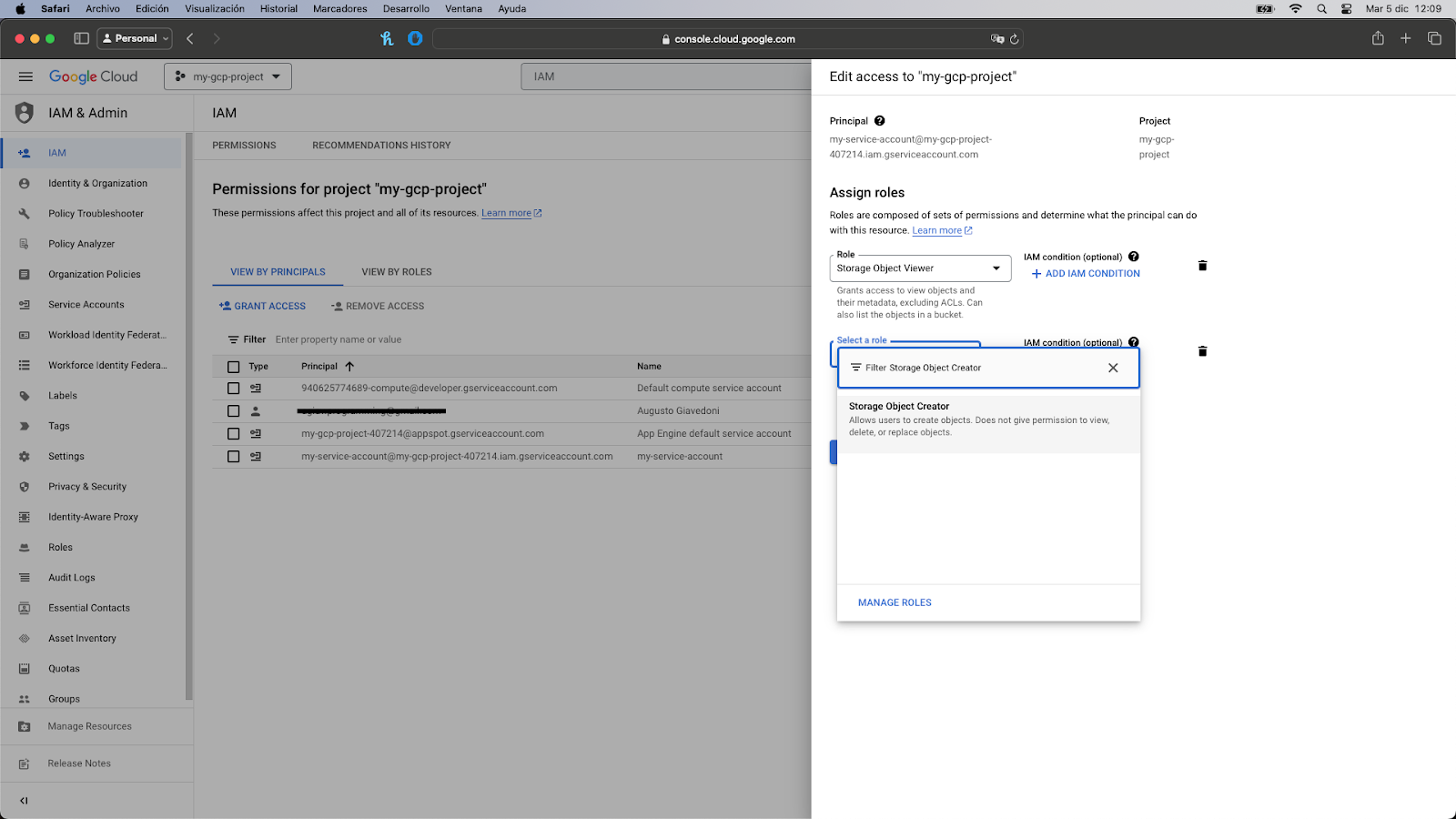
- Click on it to add it to the list and then click on the “Save” button. The window will close and you’ll see the new role associated with the service account.

Great! The service account was updated and it now has the necessary permissions to both read and write objects to a Cloud Storage bucket.
Concluding Notes
The Principle of Least Privilege stands out as a key security practice recommended by Google Cloud. Its implementation is straightforward and facilitated by IAM, which provides highly detailed control over your resources.
Following this practice provides you with the assurance of knowing that in the event an unwanted person gains unauthorized access to a service account associated with any of your resources hosted on Google Cloud, they will only have a limited set of permissions, thus constraining their actions significantly.
I hope this blog gives you a better understanding of how to improve the security of the resources you’ve located on GCP.
Happy coding!
Insights from Our Experts

Loyalty is a Product, Not a Program: How Modern Brands Build Habit-Forming Engagement
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.

Braze Intelligence Isn’t Hype—It’s a Performance Multiplier Humans Can’t Compete With
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.

Mobile Ordering That Works in the Real World: Scalable Flutter Solutions for Theme Parks, QSR, Cruise Lines & Entertainment Venues
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.


